OK…so you may have heard that’s it pretty easy to crack SAM hives using tools like Cain & Able or Ophcrack, but, you have never done it before, you don’t know where to start looking, and you feel like a dolt. No worries my friend, I am here to help.
First, download Cain from Oxid.it, and Ophcrack from Sourceforge. These files WILL be identified as malware by your AV software, so make sure you drop them into a good tools directory that is not being monitored. Creating an exception for specific files and folders is a function most (if not all) current AV releases can do, and should be done if you are working in the incident response/forensics industry since you will likely have a slew of tools that would make most AV engines freak out.
Once you have your tools downloaded, use FTK lite and extract your local SAM and SYSTEM hives. While Cain will dump your NTLM hashes from you local system, I want to show you how to do this as if you were working on an actual case. I think it goes without saying that you would NEVER install Cain or Ophcrack onto a customer system...but there...I just said it now didn't I?

Next, I simply right click, and select “Export Files”. I drop them into a specific folder on my desktop, and I am ready to roll…go ahead and close FTK Lite at this point.
Next open Cain, go to tools, and select “Syskey Decoder”…like this…

From here, you will get a popup that looks like this…click on the tripe dots and navigate to where you dropped the system hive you just copied with FTK Lite.
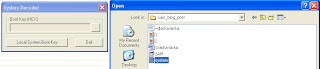
Once you click on the system hive, that little window under where it says, “Boot Key (HEX) will be populated with a long string of numbers and letters. Copy that to your clipboard as you will need it in the next step.
Now, select the “Cracker” tab, and click on the big blue plus sign that sits right beneath the “Tools” menu tab. Then navigate to the SAM hive you just copied using FTK Lite, and paste in the Syskey that you just copied to your clipboard…should look like this…

When you click “Next”, Cain will dump the NTLM hashes from the SAM hive. Your table will now be loaded with whatever user accounts are on that machine, along with the NTLM hashes.
Next, highlight whichever users you want to crack, right click, and select export. Save them to the same place you dropped your hives (for ease of use), and close Cain.
Now open Ophcrack. My .lc out put file, when I open it with Textpad, looks like this…
cepogue:"":"":E4C3436DDD1F625CEBB15F4C062DCC55:EC85B8E81AE28777453327655700B6AE
I am interested in this part only…
E4C3436DDD1F625CEBB15F4C062DCC55:EC85B8E81AE28777453327655700B6AE
THAT is the NTLM hash for the user account cepogue.
On Ophcrack, click “Load”, then “Sinlge Hash” and paste the NTLM hash you want to crack in the little window like so…

Click OK. Now simply highlight, and click “Crack”. In less than a minute, my password was cracked!

Blamo! Pretty slick huh (Yes…I changed my password for the purpose of this example)!
Now, notice that I have two little green dots at the bottom of my screen. Those indicate that I have The “XP Free Fast”, and “XP Free Small” tables loaded. These are free (as indicated by the name) and can be downloaded from the web. You can also purchase larger tabs, or create custom tabs for specific tables (like Rainbow tables, or tables you have created with a word permuter).
I pretty much do this on every case. It’s quick, and gives me a great insight into the security posture of my customer. If like the admin password is “password”, or the “sqldevadmin” password is “sqldevadmin”, I know I they were likely wide open at the time of the incident. If I can crack the passwords in under five minutes, so can the bad guys.
Also, don’t let the customer fool you and say, “oh…our passwords have ALWAYS been strong!”. Parse the SAM hive with Harlan’s RegRipper and look at the “PWD Reset Date” under that username. If it’s a recent date, A) Obviously they’ve changed it, and B) You can always go to the _system_volume_information and extract the previous SAM hive (provided the system is taking restore points or shadow volume copies. ) Then simply extract the previous SAM hive, and repeat the same steps outlined above. Once you get the previous password you can be all…dood…”You changed you password on THIS date (as evidenced by the SAM hive), and your previous password was THIS..as I was able to extract it from the previous SAM hive that I extracted from the restore point from the day before you changed the password…SUCKA!”
Happy Hunting!
Nice Chris.. I tend to share my parsed passwords with my clients for the very same reasons.
ReplyDelete